Access
Access bulk policy tester
The Access bulk policy tester is now available in the Cloudflare Zero Trust dashboard. The bulk policy tester allows you to simulate Access policies against your entire user base before and after deploying any changes. The policy tester will simulate the configured policy against each user's last seen identity and device posture (if applicable).
Cloudflare Zero Trust SCIM User and Group Provisioning Logs
Cloudflare Zero Trust SCIM provisioning now has a full audit log of all create, update and delete event from any SCIM Enabled IdP. The SCIM logs support filtering by IdP, Event type, Result and many more fields. This will help with debugging user and group update issues and questions.
SCIM logs can be found on the Zero Trust Dashboard under Logs -> SCIM provisioning.
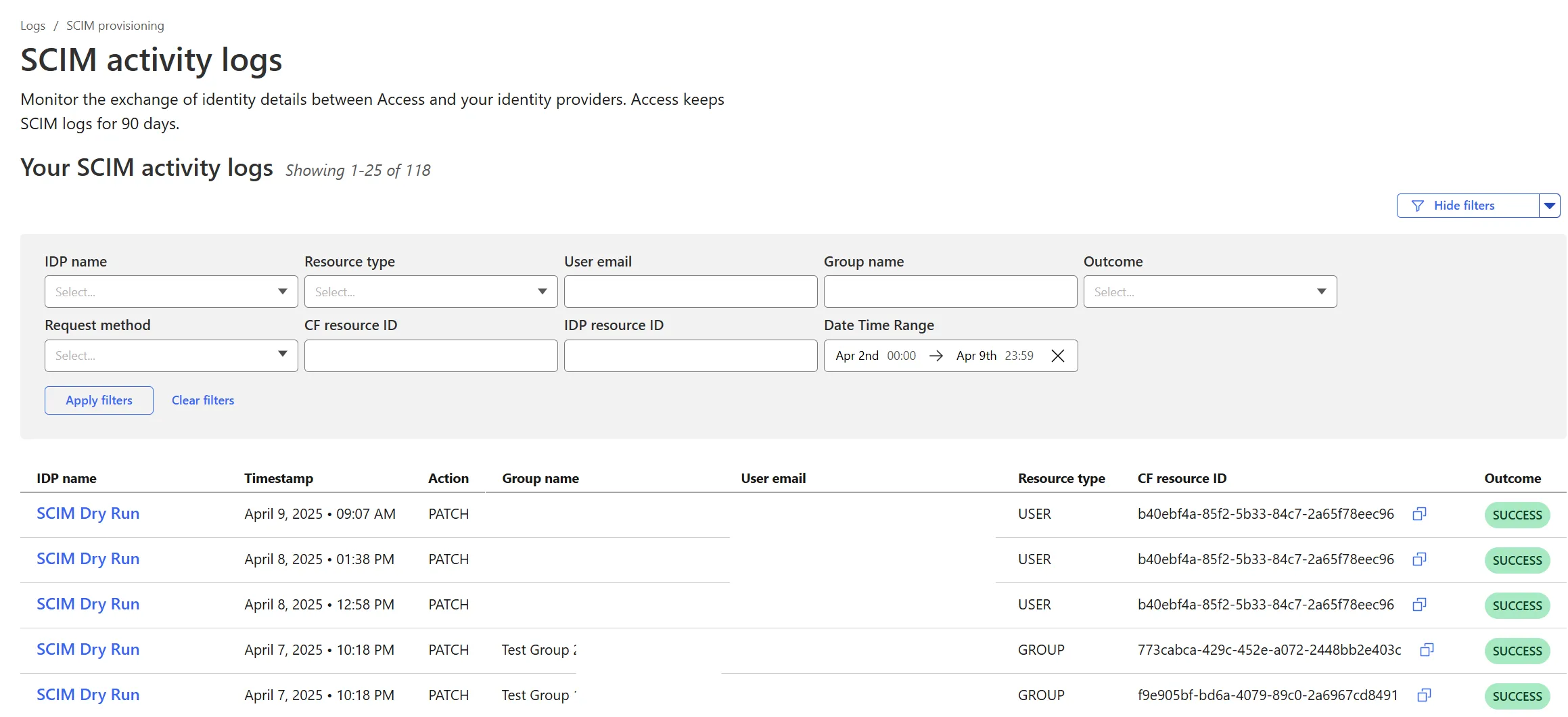
New SAML and OIDC Fields and SAML transforms for Access for SaaS
Access for SaaS applications now include more configuration options to support a wider array of SaaS applications.
SAML and OIDC Field Additions
OIDC apps now include:
- Group Filtering via RegEx
- OIDC Claim mapping from an IdP
- OIDC token lifetime control
- Advanced OIDC auth flows including hybrid and implicit flows
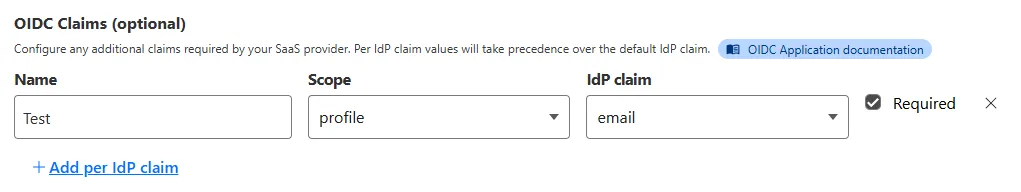
SAML apps now include improved SAML attribute mapping from an IdP.
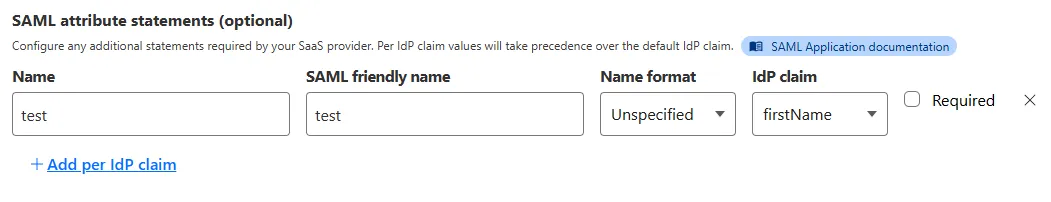
SAML transformations
SAML identities sent to Access applications can be fully customized using JSONata expressions. This allows admins to configure the precise identity SAML statement sent to a SaaS application.
Access policies support filtering
You can now filter Access policies by their action, selectors, rule groups, and assigned applications.
Private self-hosted applications and reusable policies GA
Private self-hosted applications and reusable Access policies are now generally available (GA) for all customers.
Access Applications support private hostnames/IPs and reusable Access policies.
Cloudflare Access self-hosted applications can now be defined by private IPs, private hostnames (on port 443) and public hostnames. Additionally, we made Access policies into their own object which can be reused across multiple applications. These updates involved significant updates to the overall Access dashboard experience. The updates will be slowly rolled out to different customer cohorts. If you are an Enterprise customer and would like early access, reach out to your account team.
Logpush for SSH command logs
Enterprise customers can now use Logpush to export SSH command logs for Access for Infrastructure targets.
SCIM GA for Okta and Microsoft Entra ID
Cloudflare's SCIM integrations with Okta and Microsoft Entra ID (formerly AzureAD) are now out of beta and generally available (GA) for all customers. These integrations can be used for Access and Gateway policies and Zero Trust user management. Note: This GA release does not include Dashboard SSO SCIM support.
SSH with Access for Infrastructure
Admins can now use Access for Infrastructure to manage privileged access to SSH servers. Access for Infrastructure provides improved control and visibility over who accessed what service and what they did during their SSH session. Access for Infrastructure also eliminates the risk and overhead associated with managing SSH keys by using short-lived SSH certificates to access SSH servers.
Reduce automatic seat deprovisioning minimum to 1 month, down from 2 months.
Admins can now configure Zero Trust seats to automatically expire after 1 month of user inactivity. The previous minimum was 2 months.
Scalability improvements to the App Launcher
Applications now load more quickly for customers with a large number of applications or complex policies.
Add option to bypass CORS to origin server
Access admins can defer all CORS enforcement to their origin server for specific Access applications.
Zero Trust User identity audit logs
All user identity changes via SCIM or Authentication events are logged against a user's registry identity.
Access for SaaS OIDC Support
Access for SaaS applications can be setup with OIDC as an authentication method. OIDC and SAML 2.0 are now both fully supported.
WARP as an identity source for Access
Allow users to log in to Access applications with their WARP session identity. Users need to reauthenticate based on default session durations. WARP authentication identity must be turned on in your device enrollment permissions and can be enabled on a per application basis.
Unique Entity IDs in Access for SaaS
All new Access for SaaS applications have unique Entity IDs. This allows for multiple integrations with the same SaaS provider if required. The unique Entity ID has the application audience tag appended. Existing apps are unchanged.
Default relay state support in Access for SaaS
Allows Access admins to set a default relay state on Access for SaaS apps.
App launcher supports tags and filters
Access admins can now tag applications and allow users to filter by those tags in the App Launcher.
App launcher customization
Allow Access admins to configure the App Launcher page within Zero Trust.
View active Access user identities in the dashboard and API
Access admins can now view the full contents of a user's identity and device information for all active application sessions.
Custom OIDC claims for named IdPs
Access admins can now add custom claims to the existing named IdP providers. Previously this was locked to the generic OIDC provider.
Azure AD authentication contexts
Support Azure AD authentication contexts directly in Access policies.
Custom block pages for Access applications
Allow Access admins to customize the block pages presented by Access to end users.
Was this helpful?
- Resources
- API
- New to Cloudflare?
- Products
- Sponsorships
- Open Source
- Support
- Help Center
- System Status
- Compliance
- GDPR
- Company
- cloudflare.com
- Our team
- Careers
- 2025 Cloudflare, Inc.
- Privacy Policy
- Terms of Use
- Report Security Issues
- Trademark